If you use for your home broadband connection:
- a BT Home Hub or Thomson or Alcatel SpeedTouch router (e.g. you're a BT Broadband customer) or
- a Linksys WRT54GL router or Alice Gate 2 Plus WiFi router, or
- some other router which has certain vulnerabilities (UPnP is active in the router),
Here's a list of some suggested security tips in the form of "do's & don'ts" - the scary stories after the list should be enough reason to take the list seriously and to take the precautions mentioned!
Don't -
Don't visit other websites while you're logged in to your router's main control page (or indeed perhaps any other passworded webpage), particularly if you have the LinkSys or Alice Gate router mentioned. This issue shouldn't be a problem unless you visit a very specific kind of dodgy site (e.g. through clicking an innocuous seeming link from an email or another webpage), but why take the risk?If you need to login to your router, for safety's sake don't have other webpages are open in the same browser (or indeed perhaps any other browser), and don't even think of surfing to anywhere else until you've logged out of your router interface.
Do -
1. Password protect your router
Make sure a password has to be entered to reconfigure your router, and also change the password from the standard default password that came with the router to a secure one that you've made up.BT recently prompted their users to change the password, but I don't know if that was as standard, or only if you tried to visit your router configuration page (and how often do most people do that?)
Later below is a practical guide on how to change the password on the BTHomeHub.
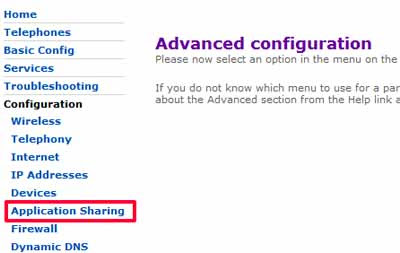
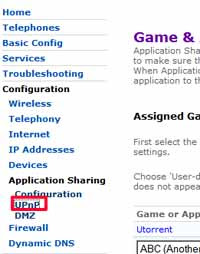
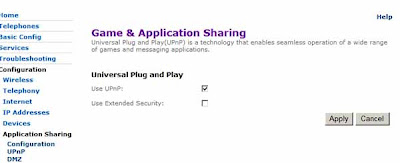
2. Deactivate UPnP
If your router has UPnP (Universal Plug & Play), disable it (unless you need to use it of course) - again, I give a step by step howto below on how to disable or deactivate UPnP on the BT HomeHub router. It should be similar for other kinds of routers, you just need to hunt around the settings and keep trying different options, hopefully the screenshots below will help.Heise Security also recommend changing the default subnet - "usually 192.168.1.0" - to another one like 192.168.23.0. Now here, I can guess what they're getting at (change the default settings to something less common so the bad guys can't figure it out so easily), but I'm less sure what they mean - change the default gateway's IP address? The IP addresses of the individual computers on your network? Anyone know?
3. Use Firefox with NoScript
Use the free Firefox browser to visit sites (rather than e.g. Internet Explorer), but in conjunction with the free NoScript add-on which blocks many kinds of attacks (including cross site scripting vulnerabilities in router logins, mentioned below).NoScript is very easy to use and lets you selectively allow only the websites you trust, do if you don't have Firefox already, consider with NoScript; and also see how to configure Outlook to open emailed links in Firefox automatically, instead of IE).
4. Be suspicious of links in emails, bulletin boards or forums, websites, chatrooms etc
Be very careful about clicking links sent in emails, posted on message boards or websites or in chatrooms etc - it may look innocent (and of course the bad guys will try their best to make you think it's legit or worth clicking), but if it sends you to a dodgy site, they can take over your browser, router, and your computer, without your realising it. Ahem, this means in particular links to porn or "software crack" sites or other illegal content offered for "free" - TANSTAAFL! Only click links you absolutely trust. Bad guys can spoof emails so that they appear to come from your friends or family. Remember the key "Don't"!If you absolutely have to click an unknown link, as mentioned above make sure you're not logged in to your router at the time. Indeed, a Gmail vulnerability - since fixed - meant that if you clicked certain malicious links while you were logged in to your Gmail account (in another browser tab or window), the attacker could then read all of your Gmail, even if you later logged out of Gmail, via a technique known as CSRF (cross site request forgery). So if you've the slightest doubt about any link, make sure you're not logged in to any passworded site before you click it, and indeed you might want to close every other browser tab & window before you click it, and make sure you visit that link using only Firefox with NoScript.
Scary stories
1. Clicking on malicious link, with un-passworded router
Mexican users were sent an email with a link, supposedly to an e-greeting card. When they clicked that link, attackers used the user's email software behind the scenes to change their router settings (if it was a particular kind of router popular in Mexico), so that if the user later tried to go to a well known Mexican banking site, they were sent instead, invisibly, to the bad guys' phishing site - which they'd set up to look just like the real banking site.So the user would unknowingly enter their user logon / password details for the banking site, and then of course the criminals had got their banking login details. This is a form of "drive by pharming". Now in that case, no password was needed to reconfigure the router, so the baddies were able to take it over.
(See Heise post for details. Making use of a HTTP GET request, if you must know!)
2. Clicking on malicious link, while logged in to router (LinkSys WRT54GL, or Alice Gate 2 Plus WiFi model, others?)
Click on a dodgy link while you're logged in to your router's configuration page, and attackers can turn off your LinkSys WRT54GL firewall, turn off your Alice Gate 2 Plus wi fi encryption, and generally open your computer up to all kinds of attacks. And also make other changes to your LinkSys router too, e.g. like perhaps like the Mexican attack above if you visit banking or similar sites.As & when LinkSys come up with a fix (they haven't yet), obviously you should upgrade!
(See Heise posts and Neohapsis for technical details.)
3. Clicking on malicious link, with UPnP active on router (it's active by default on the BTHomeHub, and perhaps SpeedTouch routers)
Making use of cross-site scripting (XSS) holes in the login dialogue of BTHomeHub etc routers, attackers could change your router settings via UPnP in order to get through your firewall and change other router configurations, and perhaps also expose you to phishing attacks to get your banking login details, as in the Mexican example.Note that even if you're using Firefox with NoScript, this particular attack may still work if there are special Flash applets on the malicious site - unless you've disabled UPnP.
(For techie details see Heise post and GnuCitizen posts.)
How to change your router password and turn off UPnP (BTHomeHub)
If you have a BTHomeHub router:- Make sure all other webpages and tabs are closed, just in case!
- Go to your router configuration page, usually http://bthomehub.home/
- To change your password
- On the left, click Basic Config, and enter your existing user name and password when prompted. (The default user and password for the HomeHub is admin and admin!)
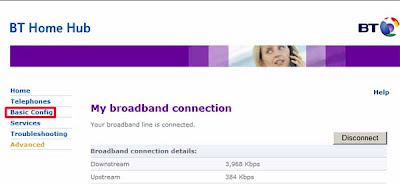
- Then under Basic Config on the left, click Admin Password:
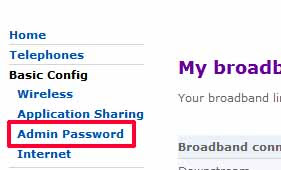
- Enter your old then new passwords, and click Change Password, and that's it. Don't forget your new password!

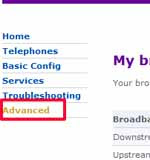
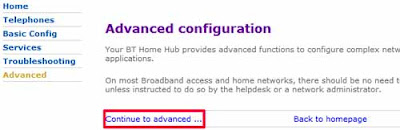
- To disable UPnP
Tags:
2 comments:
i just cant seem to get past where i need to put in a username and password...when I first logged onto the bthomhub.home page (or http://192.168.1.254 which is the same thing) it prompts me to enter the serial number for the Homehub, which is on the back of it, and then enter a new password.
Then when I click on Advanced (or Basic Config) it wants me to put in a username and password...I have tried everything, including admin/admin, admin/my new password, admin/serial number etc etc, nothing.
Any clues? Tried re-setting my router and then starting again, thinking I maybe typed the password wrong, but didnt work either.
I have exactly the same problem as Steven.
Post a Comment